Kiali
Kiali is the GUI for Istio. Kiali uses your logged in user's context when communicating with Kubernetes. When configured with OpenUnison, this means that when a user interacts with Kiali they're only able to see what their user is able to interact with in Kubernetes as limited by the cluster's RBAC policies. This makes for a better user experience and a more secure implementation. OpenUnison can provide SSO for it in three ways:
- Reverse Proxy with OpenID Connect - This scenario works the same way as OpenUnison's dashboard integration. OpenUnison's integrated reverse proxy manages the user's authentication and session, injecting an
id_tokeninto each request that Kiali will pass to your cluster. - Reverse Proxy with Impersonation - Useful on cloud managed clusters where OpenID Connect is not available, this scenario uses OpenUnison's reverse proxy to inject Kubernetes impersonation headers into each request identifying the user to the cluster.
We're quite proud of these options, as we developed the contributions to Kiali that enabled them!
Reverse Proxy With OpenID Connect
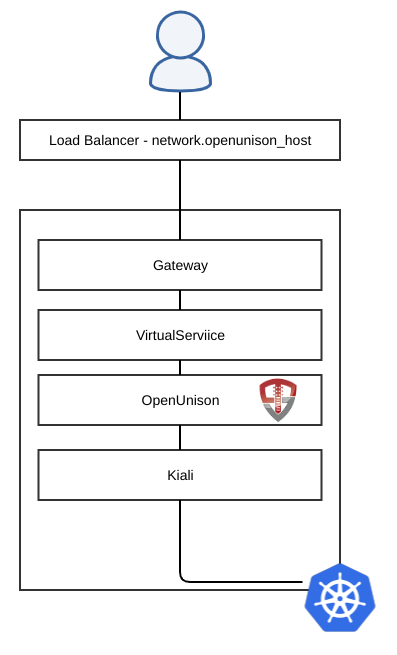
In this scenario, the user accesses Kiali through the same host name as the access portal. When the user attempts to access https://network.openunison_host/kiali the user is authenticated, if not already, with their id_token injected as a header into every request. The request is forwarded to Kiali via its Service where Kiali will then use the Impersonation headers to interact with the API server using the user's own security context. Deployment assumes that Kiali is running in the istio-system namespace.
Reverse Proxy with Impersonation

If you're runnnig a managed cluster like EKS or Civo, you'll need to use impersonation. Here, the user accesses Kiali through the same host name as the access portal. When the user attempts to access https://network.openunison_host/kiali the user is authenticated, if not already, with their user id and groups added as impersonation headers. The request is forwarded to Kiali via its Service where Kiali will then use the Impersonation headers to interact with the API server using the user's own security context. Deployment assumes that Kiali is running in the istio-system namespace.
Deployment
To deploy Kiali, you'll need to update your vaules.yaml file. You'll need a domain name for Kiali, just as you did for openunison and the dashboard. There are no differences in configuration options between the OpenID Connect integration and the impersonation integration, the helm charts do all the work for you.
First, update your values.yaml to include the Kiali application. The only two parts of this yaml that need to change for your deployment are the badgeUrl to reflect your Kiali host name and which groups you want to allow from az_groups.
openunison:
apps:
- name: kiali
label: Kiali
org: b1bf4c92-7220-4ad2-91af-ee0fe0af7312
badgeUrl: https://kiali.domain.com/kiali
injectToken: true
proxyTo: http://kiali.istio-system.svc:20001${fullURI}
az_groups:
- cn=k8s-cluster-admins,ou=Groups,DC=domain,DC=com
icon: iVBORw0KGgoAAAANSUhEUgAAANIAAADwCAYAAAB1/Tp/AAAaF3pUWHRSYXcgcHJvZmlsZSB0eXBlIGV4aWYAAHjavZppkhy5coT/4xQ6AgI7joPVTDfQ8fU5qpsz5HCkkfRMbLKrWEtmAuHhC5Du/Me/X/dv/CnJiku5ttJL8fxJPfUweNL85894v82n9/v92eHrPfv5dXe/XveBlyKP8fPfVr4+//26/TjA52HwLP/pQG19vTF/fqOnr+O3Xw70daKoK9LV7a8D9a8DxfB5w74OMD7D8qW3+uchzPM1xO+RtM8/p1+tv2vRwT7v/fL/VJm9nTlPDOFEi57f4fMuj/pnLg6eGL8ttqBnkef5/dblf66ECfndPPk/XZX7tSrH/74qP579UpRYPq87Xvh5MsuPx9++bvn3k+/eFP/pzHH9OPNPr69j9dfhfP+7dzd37/mMbqTClJavQX0P5T3jg5Mpj+9rhZ/Kv8zz+n46P82B3kXJt19+8rOsW6As15JtG3btvMdli0tM4YTKYwiLQum1FmvoYUXvqFPSj91QY487Noq5KG/k1fDjWuydt7/TLWuceBufDMbBTFBw+vWv+PnbA90ryJv59pmno/pYEAi5DFVOv/kUBbH7jaP8Jvj759c/qmukgvlNc2OAw8/PIWa2L2wJR/EVOvLBzOOn16zurwMwRZw7czEWqYAvFrMV8zWEasY8NuozOFALMYVJCSznsLnKkGIsFIeO4dx8p9r7bMjh8zKcRSFyLLFSmh4HtUoQG/ipqYGhkWNOOeeSa26551FiSSWXUmoR+Y0aa6q5llprq72OFltquZVWW3Ott9FDj5Bj7qXX3nrvY3DSwZEH3x58YIwZZpxp5llmnW32ORbwWWnlVVZdza2+xg47bnhil113232PYwconXTyKaeedvoZF6jdeNPNt9x62+13/Kiaudd29peff141+65aeJXSB+uPqvHVWr8PYaKTrJpRsZCMildVAEAH1cw3Syk4lU418z3QFTlwlVnF2aaKUcF0LORrP2r3R+V+qptL6f9Ut/BdOafS/Ssq51S6v6ncX+v2m6ptqc3y0b0KqQ01qT7SfnzgtBHakKj940f3P/3CT493/jin+98e49fH/5cDUbBWxh3lQO7tDspvZZbSA/waM9Wa1ko8UG4qroxW7wqlHyuXqR7WY2p6tvx+j5dD1lJCobBrrwHnlHgN3ICvnkNocwFIMLjaWQCfAwH53HqUXK0bOPvouaEOt/jxLtVatpRlNH59dH/3xu8eSz6UKdiOcWEO8jxAdnCRkiMwhGdbQNao5IBB07207k2WyvF7Tzpk5BomknZbywfG9wMSCuecXfIce/Y8XWnpnBpQTOt8uVtbuzb+roqBKWPDQ2VmHF/qo+xe1xqpFTtltTgL0znnbXbdKnPREPskWpt/necN7VyLa0MwVx/7xJT5dDu5H5h7Q/tjl9mv7ZvT7AE9dm2WbJmTQTS95BVnu1nWaty4N5XI+wS/ywi92Ibz65z9eAZTZwoXPul90Yzu3MRMlLDLKQ1DoYLDYBOMaCyn54p4W5i3lwllxJNhIGR/1mRtbHwHqt+322kwAL8i+NiQxGbAzGuZA2s3dwc9C+8QYaN6Y6x0PPPQafs64Nv7TDTs5R4I/RL29vU31ZkbNJtTAIVAbIwCBS3Ix8/RzoFvakfxcBlMTmq7QVP9FhfzGUtHmzBiKgGyym2iB91PdUDdY/a6Uz2WLqVMuxmEuUMenG6Ws2kaRu7qrn6uE/dpt3TPV2yH0W2XlTb+aFEvy6etg9Qy+Hr9ueGsXhlpL0Ck7b2TZ7JXriNfxnMionkH5G0C7S3n6lzql+EPJ6o4X963c8o89TJcWnTxP67MTQj6GPgoVBIsRy/Ew+oBzk6HoqQIPvtKd8KzICKsqsFn8BcH1znHrCW4hA4FUIpgLeMllIeTI7R9l0pHYTooHGSCzBSpVKnR5k3r5HRtHbV3vnW4W+eFqtcbP6elHQdHW/UKf1wTuhs7oI4bNbsZ+mGa1sbd8GYcfed0JipSR9yMrN30+pvBvXbPSiV/PGbZGC4xHTlTCxswLeQ73ppTp+WrCyj1kAtVV6Cms4PKnHePQWZ5ds67GmPJyB09fC2eE1LdfWQYtI1IU96IG4E+QLYtfxd9j+ZXJp6GubNUlKvnZZt24qUNnikfHRAGoMulD5Caovq6u42D8WeDpQlB7t2ppn94XYxi+gMPEGqS1Vp4ijE42Oyk1qjGmRd9w8xmtyCX1A8Xnpl+NJ7q6j2GCi3tTJfJCUQsNlBONuizw/XFQ4UiXd4XL0zvyuT/qHXlNaPVmNjjc9liVA568o2vfIe+j8YpYJPbjSbcZ0KZ+ALsQkdFzsXAJlwG5gbgoBDYHCYUzoQxdZk14B88hDxBz6Aye/uB9DOSUXEBh4uf7ih3YFlERepEEXGLiYlp2FpfT+ngb0HZecslIXDZVDpoAJ0bbUF9cIdbWBgOHvOFItAl3M1KADtsyCPdMahJOxij2zs4Z9ZQx+G/Pz3jwGBDt47hhdaTVITMEKBRNG8y8G0Snwj5mES3t0ADUpbGDB7NuE0tF3AQ7JgNxyCZYVrQBmQxUVcgWr2dGrfahuOCpbOUw/gEZH+nrNFKB35mwDAHJ7tOQrUx/wZ17nNP3dh+KIESzTTA9MRWBU9mh84xp3jGm+lhEkXvxDepFKVMrmZOdbmei22bFNSH23B3dCIRPRYOTfQITDe8Wy9TdPa6Az4cKC9dAyuPeLaDhXauiZYPY+EBA8MYk0YG0heZkuTDYny3fem/h61z3z6iWOY3RcUxDgTSIHWIq9wMV0jL5hj9PhRfVMhSZXbgwjXzwoGMM8WKwAe/iTbNgOte0V18KW700EoUG/mDu3K2PilugiFXqSjTicDhohn47jKnNJwJPFBsxwob0u1wtp+sXOEZCIIS4WojQLp+ns6TNmWvNlSUce49Id2JHoDFEHTNLX6gZHcQDoTZNhhFO9ZChvFIFZcykTIYAYuR/FOsihDAxHjo6IcMXYxAbHMVOzsyEkoJROk/QgtZmx4e6LhsOC3DlzqG4zQ0jd4G0ga0zkkA2itHIqqBcjgaRrqDBl3SZn10dDED00K5e8WycVJzNg9AmQyYFHDHuWFROpZG5IoG3OGY4ypDImLGVeTn7SBPJJmCcbmGdkEPxql5ZEKMTj1J7UaCUyCol6OBo8xfANMgAzgsD9xKY85SnySkpfI3ropXcSwTt9sxMANnQ2eDFsTu0JUgG3/R8ECjVhSEbqi1y6ASQHAvTICQjCQz62vSSqQxGpwOnzHa6tjhmSGWRvlBE7VA1UDZKopgfigu4WxSHeGDZ7wFWvgFbQ9fooGImhGSMH+Ay+0LsNfF10jRZWomLxluatKecVYahi49hh/kcqhmP1OJKfLQK9IN/eI43Kz+okDYUzoUnmU+cucRYzvjh6JAI2Oio+Lxq6PRa8VTaGfS3TxMNOZju0hTBNqMKbgXU0DGhJ9bPTkfqBdlDIx1ISMJ/5YqzuNj2rMcQv428ObOlFHDbpXXTMTU2LlamAA7Ujz/RUBBeLs41KPrw1H4/KDmMVCwDTGwdydHCJZwANlzYfumeBu9C/9A10jkEE9pgeQC3Q7XTxC0BqY3SHp5Z90ZlkPv+ToWIyw8aBMZU44XkXAmMOuPuDReuIXMDoxfRG4HtNLXm4pOJ/O+4VN+6JzO9cOryB/uFydSF32FJPuS722RgE0bkBgCl0f9lJF9bN1oEWyimgOWxCUcWcQhlz+n9DdDGuJRsDPBNmmDOUTv4b2q1MVZSE7Ybx9cRmNK2+TkvnAyyy79SG3o+UdmwGUHaSk6g/ODu7eyGo+U1cj8h5TDXHAgxf+6oTtZIa7Ty2fCbYSPmLcMB8zr91xZdIMpuLPKdeCLc7WrBQCfjiOJBZj4JAYLc4kjAGtGJGmLVjKqw4kS84c/5W3aBtGvsDHlpLMqJhNLNFwbuFiao3e0dFUju5A65zImaGNz8HsMExlA/jqsu4Iv6veFbkEPUHHB8YPsi3JCfYQfWhejgRjSxmRTmPH0TfNxBeCq9yw/U/wZc285EE6PG5SMNcTcEVsueHjGs47DAH4yowDQzCtd+pI2eAjQUAYucaDakB3W0SsjOjqY4HMYK4q6PMPZU1lSkCOKHXQd0zAOCQV8AHrCB6UhQgA5bK3H4GgmXAaK4yrYIGoFjqbImAkckCwr8afwr/tib81dNlt5DKqVIsWKBH361v05SJMJK8XLiiKoGoMq2cOmUB6yIwff8Lnk3ckAgMSKWbKTM6nEWQW99A9i1/AgyiF4FviKeIlBf3gAMtj1jOWiJ/BhgyOhanZG/8wtE+kuGPnV6kMjwBApoUQyhdA0NrvIoyISoRthg2yCfMEzGP8TuzmMEKSLTcEbNCg1Pg5AdZk1iHCrcg0mhoMXsQGzhhlJstB4V9rX488bFXKxQyANygGxw2/DgIB+mooAiYsgf6GXiBTylgc2j3xhHuztW6OW5kKFu3EiDsgREz0W566BS1esNxqGhMCgkQfKQ+o72uyoESmpNCDJHnZBr1D9gCfjUh2lpMGxaFpxyAurUSOZxeDt5fdSSqMJEQHkTZ2EUS9g497V6AdUdnP9MKXTQo/JA18gGBf5uK1MZsVw+gWYaUzyGgZ+fagS2Sp/6BuUORVASnfo/O5gXF9dOBLmr5OPSK+ERWgdm4Ilp3P7HoodzzXQTEjfKU0LBJPqbowWMsnMERFBG0XjjYHmI2wNZ1rhzqpD06m5MJxLEkVm6FP8fv/uUeyf+6VJH4y2yKdQrA7nFrqMmlHuuYa1qL6gGd8ii+aLltV8uYjhfhNWPwtjHn6aL14zMWuBKJRaSzoELCWBiN/4aAyTTdb/62Idqed4qBLbnqQOaD3UCFUi+LBgU2oL0YsrX5hPzykfVAxrM5ujhigUvMpXFxzsFamhIXhY+dEznyADR4cr8/SLElLSOsAkfRdkuxZ5kEXMKg3hwETUdqOYD26aZMKrMWtnj/IdAj3PO1Sf7E3BFdXgC5jQcTMuwAHzTWExI+u8RcP0lgyxH/T2vehAwJsDy6mlIFweHifwZYy6XLI3mrUnWqQB2eAJWUbewuEA7AxwKrGOThlawNnymYswFTxK1voiD5VPjfHE0f9BbOhx04JFwu+Qr7E3pmyVCMtqfNI5MqaS707+q9IXZgLaR2gLg93EQ6iWmNRebVNCRYJWGbCumGyuBDEdHR8maxbXiAaetRwJvZC1iPcdhEQMIramFCD3cU5LAPjLSiaGsBWVoXCaSxnOiF9lyDRjxa56qDbCtYcoaHQqnDmBMP1e0RJOhZgoxOGGcR7f8My8tCx8wfMLkSTIn/D550chlGuRSUkyr299twQsjVwpc5xpqKjn9YNs4KkId9Qyl8KKYm4CJeKXuIj/TMYtuArAsO2BQSvIiqgHySFDnVvcIe0FCAxzLPdL1A9roYq1Da3wYgEaCbBhq7G9YAqgpQigACJWBESQV+SwnJIQwBQuQSDvL5jitj4H59K4t3w9Vza5Nrm7TmkbtTc1V6V0S1F5kCA3qZq+62NjEKF/jGYG9HjXpKUn8J0U+4paM+FzwE+TqQNQyn3pEoZTdQrqgbSpCcJR44q5Dq1Eof2V/vg21fMnaGjTqGrNk3lsMvMZzqaTRcxNK54yO5BA+vILGGf6BY+BHdV++mEMgVzH/PSoBSsKhc9kLswNUh3V1ToqMazSqk0cLoWHrkE4hZI5OTAxgolb4QBAmSvD++ZEoE/I5HE5L8/Uy3MeLZFjMVDm36ztf9kGyIHYL9sAyMBWo0+0BuQAK4z3bAMu7cuPpCMP6x+AsVlUkrCHWlCqZvI/qAnXphyJLyHo5qpMS4mjwZ2AjvyX7YfD+K3BWLXSm7Q/rXRbpfOjRbsO967lAgBi6mPCPAhtt+Lb+8S9n6V12SG9OiGknbA1mPVBDsNZMNIckL/enLxhXdqmZYweiwHfQrpT4R7uTc9fkID8RlDx6IgPZJ14iwvYCcdR20HsXcs+IVnI+1SXpo5bMX5B4ecPW4L7etsYsJAvCClNgl8wUs8kL5JnLgwJbT1/weWW5y9QwnPReIxGByGoZCaFEZ6J+aBSy7hq295oFc+cXd6RiUgvou03y1AxtAn90BOcFbvBeeGvFgcMO2I81UjvB9fG9cPzjO68bOBwuInGhbYV8EPZ2kzhqHiZFtAbRutPSJ+Aj7NMyvdV+wedfM83sU2Ip7mFjDHPWhTEAWlWtAfbxRYIISGOsRGe4FeiM9ZQ3l2O7EEk9/UNDOcL3o2PXK7F10Tz1KyVHAzdivaWMholxTMgUBOJNH+094OHE/yG1hGZmuhK1PoaAIIsaBN6Ers/laUbg4E1sHOGh4hac4ZosLPET3HfBQ7k8NonBji6BBNj+HD4WthV5tt8dDQtlsAIyXcyOokYH/NyPIYNMJ0fOR7WwUaga7VgcuniT6iBU8p3NzwZmoKxxPdZdYwdLXsUJJr48Q5SDYM+Zu4tPvBNwoa2wxWrnk0gcyUrOwJinH9sWgtQRBsErWoGO2ktICTs/FsLcJ8ozztcOqSJyN5PkB/VTznQCgGCm4ISfLUwQljH+GlLIBOzIpBaouVIXEzEFJi5QeQek6i9oQ2h79XRJaxTSEe3JpUIKrUzozBp2nLaDo9FdBRJclbI0Po+6FcAc6QyZgZS3Zwr4Vaq9vIqWTRKsrA7WuO9Whew7jZubKmH4TyMTadg8rOzAlj65g7thbx1AcrayJ1fET5r5RL64yOEvOudNgATtulsbePBDV0nAWbaRvQZh2BanzAMhqgUt7wz/YghVXUgFmvvPhcHddnVZq8kmQFniBk6r57GSOGSvOHzg/KQd2whGFF7K1qGxpUrUwBsbZ64l+Cr1jJr/VoFi5GQMDBGByhXhNETSi+sgk9lOpHDYp3LBGa2iGQ47HwdHonIccK5+NOSZKY4Ve4gBrVEUW57d1IQTuXcWtKGTFfas1bJkFoE5YKn65Hs7deZla6D8UDB8YQF3O4492OoQPaBvbQPl1AbhZF3g0SnaCERhWAVMm37rAYAPNOmGe4M51WRQ0ZdJfWyuBtWYfhoddadFrExeHkjGQgS/PCuG12+xNpGQhqeeSMs0uQL4GiL9i0oJZH4M85lHYSynuf+kHIkDdid4KDht8AF43oSDCgt07QbIB1Gq3TPiORQWyp4PwZ1s/ZJlhSEySCIY7RsItnYuANVd67NrhQEq4ab55pVWyqsXfFtSSPj8hJdtunozlkhA7i1HdKv011h2kuB7JQjK3MIlxBHgQvVHZMpvDD3eXspMLgW1UvWrSZax9NaEMYaN9Jq070g2nhupdOsveqOBSxXWsRIk8ndWufBMGLrOSOUBySY9E6TieKDlN6pYrjigIOuPcnHQAVj4NrTAYZ4eK3Kb4IRVidhipqBwvRqqvFn3QzQZ3AY7OK1rhAi7itPBZcX1RIJi/i3GtGB4StwxqQF44vGYqlRCdI2k5DIDr26vdSnW5v/lSbD62zyC2eBDvs0DI5uFbqah3Li81EFcyjPI3KfSlkEmOSuFkogogWjmrbAStGCvu5XEosCCi0T34Qp1sLi0t115XUf9usW3SRQiFrZmZaj8UaSxqPVVGSWC54ZT5joALtfdulCTH/eci1q56El5GOHOSIzD50RTwHfI+tS1aiV3VxIx1gY8hC28cGlbI/GMepNNtrDFLDhOMxCdhB2bRiBdmVmOIwiIgRm5JsQXh7WVimqSWERG4yYVUlmZwQHH3yhAlKk0+J6QJLpwq89lyN9ikyEtlwC9ljLjQ0HU2wmvy8eWre8ys5ML94l087hdH/SQAijhPDtyRHWY8RUYojklCErpEOuYDfC+zi9ZczxxkBkspyWvCZE6L53V/zW0qF2V3Cy0jmqC4OPrc4I2l3hGVmP1Dc3eFDQprnh3C5fMR3TR5KnkDAVBoOYEpl13ciCkGp3q3/dzca8b3I6LQYcIdJM/eEZIlEe746oCWvOPxZy/rtHqiQBwpfAfcghci7/XlzuQ/cbaoO80IBIZGpHUNYKM3NHrMFbet2HJOOnTd2Ls9+ZdC1nBw/CuHC2/FCjZBAvNrMscRIkblr478yPduGjFkdQ5NE/a8m69XFKuYjV33fvINnP92LpU9Ga3jbd8rEnkawTz/bbw4MjcfWROpVrQ0vcHHqhGXgyI8nesR0cgcUx3T8DjQJg3T9RDv0DHG+0AjOLZnSLK9hoUhQtE9TlgVvYMBQBCRWRM4eRuQ7UlZy1dYtPmEv3KMDiWmZPuSlPkC4DIZ1x4X2bbmZKKaC8igk7uqdNuqmjvsgbEFgqQgyhRxYBcBTYDNIaaDlj3xoO3g9Om6qfVm4wGM+wgysph+6Deg+6mXvD5w3MgEMytVcLRzAMgV+KAXXodgneBVWm23Xn1hIr3/rcPROmboSi4LrjdAsY3lBgmVwzGcDwbp5BEOD9sYNuYpE9BknTpbdljiU4G+CACN0LRVfRI4eT+giStae5kgxU1301Jb+n+RStQGphgrl174sApJB7tWIT1Xm6E6PknaASQBFsQ7go0nMLi/nVNr4BkaEVC4+4+euoPuwdFNJJ1XZkw70XRje+Q0uzRDsmg0wP06EgujuM1NJLQxKL7ptJG7w63SQEVfRWtIB7+OiounEGouNlWCdrF+vrvhnEIeq+Cd03Izfa4Y6tzfX8TEQ7OuV4uWboxhklat2ehetQ3YYYUju3IhVmAWMC1XivfURtoS+t1jvdijLADtElagn2y7WFWP85I+jR/f0H5HCxw4ATlQfNI5PTBk5Htw9hfLWI2jCyMHKLzWEWwSAJQQsnh19YxWdz/GcBTOvDfG9ghkPRfvrK4hHokWnNCUctJ9STo2BRQTvPiHTkgHky3TVjg0TPAXL1CW/Rvta6yu9uKtKj+7s3/qeP//hAdf3XH3H/gov5y4Egg93dfwKF22SyCToLIwAAAYRpQ0NQSUNDIHByb2ZpbGUAAHicfZE9SMNQFIVPU0WRiqAFRRwyVCcLYkUctQpFqBBqhVYdTF76B00akhQXR8G14ODPYtXBxVlXB1dBEPwBcXNzUnSREu9LCi1ivOGRj/PuObx3HyDUy0yzOiYATbfNVCIuZrKrYtcrAuinL4ZBmVnGnCQl4Vtf99RNdRflWf59f1avmrMYEBCJZ5lh2sQbxNObtsF5nzjMirJKfE48btIBiR+5rnj8xrngssAzw2Y6NU8cJhYLbay0MSuaGvEUcUTVdMoXMh6rnLc4a+Uqa56T3zCU01eWuU5rBAksYgkSRCioooQybETpr5NiIUX7cR//sOuXyKWQqwRGjgVUoEF2/eBv8Hu2Vj426SWF4kDni+N8jAJdu0Cj5jjfx47TOAGCz8CV3vJX6sDMJ+m1lhY5Avq2gYvrlqbsAZc7wNCTIZuyKwVpCfk88H5Gz5QFBm6BnjVvbs19nD4AaZpV8gY4OATGCpS97nPv7va5/dvTnN8PgftyrXck/CcAAA+LaVRYdFhNTDpjb20uYWRvYmUueG1wAAAAAAA8P3hwYWNrZXQgYmVnaW49Iu+7vyIgaWQ9Ilc1TTBNcENlaGlIenJlU3pOVGN6a2M5ZCI/Pgo8eDp4bXBtZXRhIHhtbG5zOng9ImFkb2JlOm5zOm1ldGEvIiB4OnhtcHRrPSJYTVAgQ29yZSA0LjQuMC1FeGl2MiI+CiA8cmRmOlJERiB4bWxuczpyZGY9Imh0dHA6Ly93d3cudzMub3JnLzE5OTkvMDIvMjItcmRmLXN5bnRheC1ucyMiPgogIDxyZGY6RGVzY3JpcHRpb24gcmRmOmFib3V0PSIiCiAgICB4bWxuczppcHRjRXh0PSJodHRwOi8vaXB0Yy5vcmcvc3RkL0lwdGM0eG1wRXh0LzIwMDgtMDItMjkvIgogICAgeG1sbnM6eG1wTU09Imh0dHA6Ly9ucy5hZG9iZS5jb20veGFwLzEuMC9tbS8iCiAgICB4bWxuczpzdEV2dD0iaHR0cDovL25zLmFkb2JlLmNvbS94YXAvMS4wL3NUeXBlL1Jlc291cmNlRXZlbnQjIgogICAgeG1sbnM6cGx1cz0iaHR0cDovL25zLnVzZXBsdXMub3JnL2xkZi94bXAvMS4wLyIKICAgIHhtbG5zOkdJTVA9Imh0dHA6Ly93d3cuZ2ltcC5vcmcveG1wLyIKICAgIHhtbG5zOmRjPSJodHRwOi8vcHVybC5vcmcvZGMvZWxlbWVudHMvMS4xLyIKICAgIHhtbG5zOnRpZmY9Imh0dHA6Ly9ucy5hZG9iZS5jb20vdGlmZi8xLjAvIgogICAgeG1sbnM6eG1wPSJodHRwOi8vbnMuYWRvYmUuY29tL3hhcC8xLjAvIgogICB4bXBNTTpEb2N1bWVudElEPSJnaW1wOmRvY2lkOmdpbXA6YTRkMzkzZTgtMzAyYy00NTA0LWFmYTgtYzVmMWJiMGEwYWVkIgogICB4bXBNTTpJbnN0YW5jZUlEPSJ4bXAuaWlkOjhmZmNkNjg3LWFmOGEtNDM5ZC04NzI4LTg3NTRkMTYyOTIxNyIKICAgeG1wTU06T3JpZ2luYWxEb2N1bWVudElEPSJ4bXAuZGlkOjBjMGY3MDc1LTQzYTktNDcyMS1iNjAwLTMyYjA0MTUwMDQ3MCIKICAgR0lNUDpBUEk9IjIuMCIKICAgR0lNUDpQbGF0Zm9ybT0iTGludXgiCiAgIEdJTVA6VGltZVN0YW1wPSIxNjEwOTk1OTg0MDQyOTA2IgogICBHSU1QOlZlcnNpb249IjIuMTAuMjIiCiAgIGRjOkZvcm1hdD0iaW1hZ2UvcG5nIgogICB0aWZmOk9yaWVudGF0aW9uPSIxIgogICB4bXA6Q3JlYXRvclRvb2w9IkdJTVAgMi4xMCI+CiAgIDxpcHRjRXh0OkxvY2F0aW9uQ3JlYXRlZD4KICAgIDxyZGY6QmFnLz4KICAgPC9pcHRjRXh0OkxvY2F0aW9uQ3JlYXRlZD4KICAgPGlwdGNFeHQ6TG9jYXRpb25TaG93bj4KICAgIDxyZGY6QmFnLz4KICAgPC9pcHRjRXh0OkxvY2F0aW9uU2hvd24+CiAgIDxpcHRjRXh0OkFydHdvcmtPck9iamVjdD4KICAgIDxyZGY6QmFnLz4KICAgPC9pcHRjRXh0OkFydHdvcmtPck9iamVjdD4KICAgPGlwdGNFeHQ6UmVnaXN0cnlJZD4KICAgIDxyZGY6QmFnLz4KICAgPC9pcHRjRXh0OlJlZ2lzdHJ5SWQ+CiAgIDx4bXBNTTpIaXN0b3J5PgogICAgPHJkZjpTZXE+CiAgICAgPHJkZjpsaQogICAgICBzdEV2dDphY3Rpb249InNhdmVkIgogICAgICBzdEV2dDpjaGFuZ2VkPSIvIgogICAgICBzdEV2dDppbnN0YW5jZUlEPSJ4bXAuaWlkOmJiYzdhMWQ2LWQ3NmItNDk5Ni1iNGU3LWM2ZWU2YTU1Y2E2NyIKICAgICAgc3RFdnQ6c29mdHdhcmVBZ2VudD0iR2ltcCAyLjEwIChMaW51eCkiCiAgICAgIHN0RXZ0OndoZW49Ii0wNTowMCIvPgogICAgPC9yZGY6U2VxPgogICA8L3htcE1NOkhpc3Rvcnk+CiAgIDxwbHVzOkltYWdlU3VwcGxpZXI+CiAgICA8cmRmOlNlcS8+CiAgIDwvcGx1czpJbWFnZVN1cHBsaWVyPgogICA8cGx1czpJbWFnZUNyZWF0b3I+CiAgICA8cmRmOlNlcS8+CiAgIDwvcGx1czpJbWFnZUNyZWF0b3I+CiAgIDxwbHVzOkNvcHlyaWdodE93bmVyPgogICAgPHJkZjpTZXEvPgogICA8L3BsdXM6Q29weXJpZ2h0T3duZXI+CiAgIDxwbHVzOkxpY2Vuc29yPgogICAgPHJkZjpTZXEvPgogICA8L3BsdXM6TGljZW5zb3I+CiAgPC9yZGY6RGVzY3JpcHRpb24+CiA8L3JkZjpSREY+CjwveDp4bXBtZXRhPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgCjw/eHBhY2tldCBlbmQ9InciPz40AsVaAAAABmJLR0QA/wD/AP+gvaeTAAAACXBIWXMAAAsSAAALEgHS3X78AAAAB3RJTUUH5QESEjUE99PnhAAAGw9JREFUeNrtnXuUVMWdxz91u5sZhuE1vB+iTkMUEbFnUBQj4NqDmIcm8YXoZjfBmGNCezzZ3TyOyWazSXaPm8fm2Gg22Wh2N9nVkHiMSVwVOokmK4kKNKAoCo2CIo/BkRmGYZiZvrV/VKujAnb1Y6b71u9zjsej59btub9b31u/qvrV7weCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAiCIAwkSkzgHkOaWrw+rRs0jAZGASOAOqAGCOcuywJHgS6gA2hX0BZSqq13w5qsWFGE5AQ1TS1ej9aNwCzgdGAG0AicDEzKicazvK0P9AB7gZ3Ai8ALwFbg2bBS210VmQgpIHix+GgN84ELgHlAEzBygN9xB7AReAJYq+BxP51qFSEJFUukqSXUp/U84FJgMRADIhX2Z2aBTUAK+N+QYm3fhlSvCEkYVMJNLeGs1guBa4AP5Vy0auIA8CCwylOkshtSPSIkYeBeUiw+E/gEsAyYEpDH2gesAu4eGQ5tOvjUI1qEJJScUFN8iK/5CPAZ4MICFgaqiSeBOxX8zE+nukVIQikWDUZo+BRwMzDNscffC9yh4E4/nWoTIQmFCGiUhgRwC9DguDk6gJUK/tVPpw6IkIR8BFSn4bPAF4AxYpF3Ceq7OUF1iJCEdzG0ucXr9vU1wD9jNkmFE7t8Xw4r9R+VuuErQhoMo8fiZwFJYIFYw4p1wAqdTj0hQnLbjRuq4e+Bv2HgN0+zwC5gOya85xXMEnQr0A50Akfe0aYWGIaJyRsDTACm5kbQ6bl/hwfhOe5UcKufTh0SIbk3Cp0H3AWcMQA/5wPPAWtzX/GNCp7106nOMnwYzgDOBpqB84EzB0hcLwE36HTqtyIkBwg3xSNZzZeBL5V5FNoNPASsVvDoYMW4ebF4gzYuawvwgdyopcr4wbhdwZcGe/9JhFTeUWga8N/A+8v0E7sw0QH3RZR6smfDGr+Snr+uebE64vsx4GPAUiBapp9KA9fqdOp5EVLwRHQJ8FNgbIlv3Q3cD9wVVurRajm2UNvc4h319Xzgk8DVublXKWkHPqXTqZ+LkAJA7iv8eeAbJZ0rTJjhM/qke9n6u8/pdGpflS+6NGgTO5igtEv/PnBbWKmvDPQHRoRUQkKxeK0PPwA+XrKbTp3j67MWw4RGD+UdAq4gEV0TCHuZeMJrcvPHmSW89QMKri/14ooIaeC+svcBi0pyw4mn+br5Mhgf9VDqna7dMhLR+4Niu9zxkKXA1zCneEvBOuDDOp3aK0KqnvnQFMyK2eyib1Y/Tut5V2mmzVYo73jvpwe4jkT0FwEc0VcAt2JySRRLBlii06ntIqTKF1EjsJpiV6SUB7HLfT1rkSJSm897CaSYcjadCPwLcH0J+uirOTE9LUKq3Bc+HfgtxR53mPA+redfqxk92fbMUU9uzvSbgNp3MfD9Erh7+4EWnU5tFiEdh5pkxuuBGm1cgbrcPwC9QLeCjhC01yrld65o1CV8yY3A74sSkVIw90pfn7FQEYoU+i4OA5eSiP4xoHPPERq+Aywvsr/uB+LlGpmqRkgqmRmuTYKPOZj0UtNznXgSJi/b8Z5HA32YmLJXeCuF1BYgHYHtvYmobymiycAfinLnho/XetFyzbhTSnHytQ1YQCK6JcCj/xXADynurNZu4CKdTm1zRkgqmanXcBEQxxy1PpPyhNi0An8CHgUeqVVs7V5xfGHl0l49VtTCwinn+Hr+UkVtfSnt/yJwPonovgCL6VRMJMfcIhcgLtTp1J7ACkklMyM0XIbZ+b64n5s2kGwDfgncU6fY2LUi+qY7GIrFa3x4mGKWuJs+6uuzWhReqBy2f9yDi/1E9GhQxZQLlP03iturW6/golJGjw+6kOpX7lCdJj/bp4ErgOEV9N42A3cp+En93csPdhL+MfBXhfWAEHrh8iynNofK/Df/O4nojUFe5BnWvFh1+f4XMdEjhbrGvwor9bFSRUAMmpBCyUw4C5cDfwecW+HztUNqy+//xBP3Li6odWSo1i2f1UycMVCZgG4gEb2LgKNi8euBH2HSLxfCbTqd+mJVCimSzHi9ZuT5GqUNCykfHa1a/eqfoKfL3l61w9FLbvFpmDqQ6bS6cvOlzQ6IaQkmoqSQaYCPiRpfVV1CSmYuxCxlnlM1b6r3qFYPfw9ad9jbqm6U1pfcAqMnDcZou0XBPJ2IHnZATAuBXxc4LegA5ul0amtRc7cBWkQYTzLzX5iVseoRERq14Te6IBHVDmcQRQQwS8NtOIBOpx7DpHDuKqD5COBeLxYfWtlCSmaWangG+EuqLVvormd8tqy2/5sjtVovucUfRBG9wU0kM4sdEdMfMFOGQlYs5xT70Snbi1bJzEgNdwDXVeWb6Tqo1f1fh6OddjZSHvrSz/kDuLDwXuxUMFsnoodcEJSKxZcBP6Gw2k+X6nRqdeWMSMnM2RqeqloRaR/15P32IgL0wuWVJCKAkzV8E0fQ6dT/YKLHC9HCD71YfGRlCCmZWQo8jqkQV53setpnx5/tR+umj/g0zq1E9/Umkpm5rohpWMi7DfjPAj86/zyort3wlTvUIa1vxSxrV2/lhO5Ore7/RzjSbmebU+b6etEnyxWxUAr+HIELbOMKqxUvFq/NhXKda9k0CyzQ6dTaAR+RIslM6JDWdwBfp8rLj6in12hrEQ0fp/X8aytZRADn9Varq10AufRc1wCvWTYNAclwU0t4QIUUSmbCvfBj4Kaqt37bbp9nHrGziVLohct1iQNQy8U3VTJT54qYdDr1EnAD5gSAlZOe1fqGARNSOJkJZeFuzNJ2lVtda7X+AYW2tHnzFT7jT62WUfikXOkYHBLTLzHHL2z5B5uFh4I7QP3KHaoPbg+EiAD2PK95eZPdqDJ+htazFlXb4ci/U8nMSJfEpEw8Z8ay2QRt2pVXSJ1mYeEzwXCos1qt/5X9ftH8a3URJ1sHizGujUq54xKfLsDFuzmXP6JMQjJL3F8LjKVf3QqtGTtBnP1hn4Yp1bqwcotKZoa7JKZcsn3bJfHhwN+WR0jJzNmY0PVgFAfWvlbpB+3aDBuj9ayLqjnfxRhtJuFOoUxVRNvatJ/2YvFxJRVSzrdeRenzNg/i3Gibth2N9LyrNUOGVnvimJu9ZCbikpD8dGo/8I+2ywHa5NorjZDG3bFD5WLnZgTJuGqLZXmd8TNM8sbq5xTfHKx0Cs+k97JNfvIZLxYfVhIhtZp6p8Ha0Hv9VZ+XN1mNyrr5cl3hG6823OSakLLpVA/wVctmYzVcW7SQVDIzAbPUHSyfefuTdg0mn6GZGPUCZIJFJDOnuSamiFI/AzbZjkrj5y1RRQlJw7eBcYGyZk+Xz3O/sxuN5lyqUUHSER6FJnOp5ldvCrLZnj86u7Wn75zChZTMLACWBc6au7cq+izOgI1r1EycHsQUz9eHkpmwa2IKKfVz7DZpFaamk72QIslMCPguQVnq7m+VbWutNuf07Ev0CapDVDMnZctXmrNi6duwpg9IWja72ovFa62F1GsSNTYHzoqdbT6vPJP/x6F2hGbqzCAXHLgKB1HwH5jkJ/nSoOESKyGFzB7DVwNpwD3PYxUtMiuuCdcEWUgfddG989OpduBey2bXWAkpC1cCwVzRydit1umT5wS9T03KFpdPu5qxTaR56bHcu2MKaejKjMIi8rWq6Gr32fNc/m7dhNN8Rk3wHOhQH3RRRTWeWgc8Z9FklDZFHd5bSEc0F2JKqASPAzuxOnM043wcqce2xEUhda9f4xfg3n0wX9fus4GdYL5ql1BTT36fK31qjkpmxjrq3v3CbtJMy3sKKWfMDwdzdpnVvLgu/+FlXNSnvsFzpDNFNMx3UUV1Ie857OLvTlex+KQTCkmbRYahgbRYZ5tdYpNT5+JYmd0LXRTS4XWrNfC/Fk08YMF7uXZLA2ux11+1c+smRF3rU+fjLo9YXn/BcYWkkpnxBHh4Vwd25n9xKKIZPcm1znSWl8zUuKgiZcqf2uQNn3dcIWlYTHnqtFYGe57P/9opZ2rCQzzH+tNwv5gC09U8fTabszb1pGaFYvGa47l2lwTWUn1HfV7bmf+EZ+IMHGUO7vK4xbXD/H6HXN8U0pBkxgMWBndG2Q7Z3ryFpBumaEc70yyHhbTO1hV+l5B64CTMP8Gk0zLnxYjxrnam0x0WUtry+pnHcu3OC/RkstMiBXS4RlM3wnO0M013VUUe7ACOFGKr/p3l7EBb6dCB/F21MdM0Xlg52p+mhs05NOfImsT7L1k0aTyWkM4MtpBa87+2YarD3g0NWah3+PlfsLj2pKHNLd47hRTsoLKDe/J31YaP0w53JKVhosPPbzMije3xdeRNIeUO8QX3M+xnfbra8xaHHjoCx5ng8LO/bHFtxIcxbwopa/4juHVzsn0eRzstjpbXe44LaZzDz76vEFu90WGCHQuT7e01RavzZMjQrONCGuXwsx+wvH50fyGNCbRp+no8qyjuSK1yXEjDHX729kJs9YaQgl14Kttnt5zrhUKOC6nW4WfvtLx+WH8hBbuuqLYs5O2FtONCqnP42bstr4/0F5Lrrkx/1UEo3Cd2cJbeQhp5b/UeQRAKQPUXktDfLtm+sNjBWWzP4+n+QuoKtjYsvxd+1nVXt8vhZ7ddaOntL6T2QJsmFM5aCsn1faRuh5/dNs7wcH8hvRZo04SH+FbTwN5u1+eMhxx+9pGF2OoNIe0J9ogUiVhNB3uOuL6P9LrDzz62EFuZoFUzIgXXLw6FfWrq899M6u70HRfSAYef3TZgt/VNIWUT0V7glcCaxgt51I3MewFBHelwXEfWgZtBwibdQq+Xmxb193deCLR5Rk3Kf5Q5dMDlbQGtYK/Dz3+Kzcg9xFO97xTSM4E2z3CLkwFtL7u82NAWso83CxI2B1xfPmKqWbxNSBuDLaSx+e8NvbZL4fe5KqZX+hJRJ5f/cwkfbUakHW/OHvr9zz8H2l+ptzgp0ndU0dXh6oLDdleHolyW2aGF2OqtBJHmiO2uwFqpvsHu+o79rvanrbiLbXG9594lpJ5E1Af+EFgTDRtpEuPniWrb7WqY0BaHhWRbR3fzsVw7sC9tUT2EazzGnJz/vGfvNlc70yaHhXSBxbWHvX7Fyd5e1sUIqTewZppkUaR99zOKvh7X5kmHPMi4qCAvFh9Jv1ze+Yzc2XTq6DGFpBPRVmBtYBccxp6c/8XZXsXre1zrT5v9RPSoi0LSpsiaTW2oJ94mxGNccG9grTV6stXlap9zH+c/OezW2ZY0evyEQlKmwvORQJqqvkExdGT+86QX1+HY4eE/uqigYXMXK+ADFk3etTD37mLMiegB4NfBdIRDilPn5q+M1oxHZ5sr86ReFWC3/kR0Zf2Z9CsalgdbdTq1571cO4A7AusLT7Yr/6NefcGV/rQ59xF1kSuxSwC05l3f6GNdNVTxR+yLLlUHY08GZWGzbX9yxb17yEUF1ZpqEkstmz2Yl5COrIhq4FuBtFzdSI9JM/N31/Y973Fwnwvu3YMuCumor5vpV3kvDw6qY8wlj3tcIGQWHZ4PpPUaz7Vz73YGfo9yT8i+fmpQuMF25PZNQbL8hJQ77Pe1YM6TTrNzibekFH1Hg+zf3Z9NRJ1LipnbhLV16352zHudqEUEVgHrA2fB+gaPqWdaHD3vULzyXJCF9HMXhyINfw3YFMNqU8cJozuhkHrNuZTPYVUTpUqMOGO+VVCqevoRhfaDKKaXQ/B/roko3NQSBhKWzVYdy617TyEBkIj+AfifwFlyyumasEVESOsOxd7tQRTST11067JaX4U5f2QxgPHj47qJeX2N4W/JZUsJDEPqPGb+hdVIqzY9pKwrW1Q2PvCfroloSFOLB3zBstnGcUPCTxUlJJ2I7gNuDpx7N91u9Y5Xn1XszQRJSY+SiD7vmpB6tb4GmGPZ7M79TzysixJSzsW7F/jvQFl09GSPk+bYjUrrH1D42aC4eN93TUShWHwI9qvRBxTcc6ILrNJOKfgs/Q4zBWJUmnWxXYP92xS7ng6CkF7y4AHXhOTDTdjF1QHc6adTh0smJJ2ItgNXk0scHggmzVCMi1oJQz2xStFzpNrFdLtv9gqdwYvFxwN/b9msU8HK97y39V+TiG7E7AYHY66gPKVjH7Rrc/g1pbb8vpqF9JqCH7k2Gmm4DbDMgsMP/HSqtfRCemu+9NXAWHjy6dajEht/7dG2u1o/Jt/TiahTFSdULH4x8FeWzQ4B385rtCv0D6tX6pvAncEY80Po5svshKR91Np7FNneahuZXlOQdMylGw78APtaybfrdGpvWYXUuaJRh82S+E+CMVc6TXHSHDtR7N+m1JZHq01I38rNdV1y6b6F3eYrwD5lcQKiqGTxfYloNgSfDISYlFK6+XJtdVYJYP19HvtfrBYX72XXRiMVi38EuLGApv/gp1PtAyIkgGwi2heBTwTCzWuY4nHmJXai0Br12F2K7s5qGJlu1Ylol0MiOgWzqGLr0m0IKWW1GFOS8iW9iWh2hFIrgK9Q5at5enaLXYIUgEOtSq29R1f4Ru2fI0HbUD/xvGgo5sjDGMumWSDRt2FN34ALCaBjRaMmEf0GcB3VvM9UW6/0/OvsBfHSOk9tXl2pQuoDEr0mLXXgqZ+7WGnjIZ1bQPMf6nTKOglM6QtqmaXx91PNERDTZns0nmcvig2/9NixvhI76/dJRJ05AXs4638ec9bIlp0KvlTQCFiWJ0lENyo4h2p1JZSHPvejUFNvLSb12I889m6rJDHtVHCrQ/OiZcA/FdDUB260WWAov5DIhRMlotcD11KNRzDqRil94V/bj0raR61ZqWh7pRLE5AM3urL5qmLxJcDdBfbrO3Q6tbrgOVnZny4RvVfBmZgl8ury0aed6TFrsf3f3Nut1MPf83h9z2DPmb5PIrraEREtAO7DLn/3G2xS9ueTBlhIZnTaTyL6cWAR8FQVvR5004cU4xrtBdF9CPXI9xhEMW0ptnNUmYh+A9QV0LwDWOqnU0cqXkj9Rqc/RuA8TAT5c1XxliI1Si/8JAypsxdE10GlHvrOYLh5XcAynYgedkBESzDJLYcX6Pp+SqdTRVcp9Ab6wXsTUZ9E9OchU4vmSkx5jMrezBwxrpPYZWsKatt9CPXgt9UAL0DcTCK62QERXQf8ssCRCOBbOp1aVRrfZZCpX7lDdWo9D/g0cEWBX5ZysRm4S8FP6u9efrCT8I+xjyDOfbJC6IXLs5zaHCrz3/zvJKI3BllAw5oXqy7f/yLwjSIGg1+FlfpY74Y12UAI6W1/TDIzQsNlwFVAvIgvTTFsy33l7qlTbOxa8dbxilAsXuPDw7m5XmE0fdTXZ7UovFA5bP+4BxcHuViYF4sP1fBvwMeLuM16BRf56VTJVjMrtuCwSmbqNVyUE9SFmJW/SBl+qhVTYOtR4OFaxfPdK44fAeDF4qM1PAbMLvgXTznH1/OXKmrrS2n/F4HzMYlqgurKnYpJWjq3iNtkgAvfWZYlsEI6hrCGa1O+fQ5wOjAdmAZM4q1smcd6Ho0JkWkFXsl1uBcw1bvTEdhuGzqjYvHJmEJT0YIfaPh4rRct14w7pRTz1DZgAYnolgCL6Argh9ifcO3PbmCRTqe2l/zvq3YD1yQzXg/UaBiVcwXfcAd7gW4FHSFor1XK71zRqEv4YhuB3+fEXOBNFMy90tdnLFSEIoW+i8PApSSigay258XiIzR8B1heZH/dD8R1OvV0WYSOUIyYpgO/LUpMABPep/X8azWjJ9uOTj3AFSSivwmofRdjUoY1Fnmr/UCLTqfKtpIpQirNyLS6KDcPQHnQdLmvz1ikiNSqPEV0HYnoLwJo04nAvwDXl6CPvgosKddIJEIq7YufgtkUnF30zerHaT3vKs202QrlKZdEFIrFa31YgQmyHVWCW2ZyItpe9j4gMiiZL9+gTazXopLccOJpvm6+DMZHvXccf+8GlpGI3h8U24WbWsJZrZdiMqA2lui264AP55u8RIRUeV/UH1DcHsfbmTrH12cthgmNHso7lJsTrQmEvZriQ3zNNZgzQDNLeOsHFFzvp1OdA+aVSPcvLXXNi9UR3/88Ztc9XLIbT5jhM/qke9n6u8/pdKqq94pyo/cnMPWJTi7hrX3gtrBSXylVxIIIafDnTZcAPwXGlvjW3cD9wF1hpR4d6A5TKLXNLd5RX8/HZJ26GhhW4p9oxwSgDkr1QRFSecU0DXNK+P1l+oldmJ3++yJKPdmzYU1FnffKjc4x4GOYWq3RMv1UGrhWp1ODVqJGhFT2iXQ8ktV8OTcPiJTxp3ZjVg5XK3g0n3zVZXTbFgAtwAdyrlu5+pkP3K7gS8crSSlCCt7odB5wF3DGAPxcFtgKrMWsXm1U8GypJ9+5ANIzgLOBZuB8TExkeACe8SXgBp1O/bYi3q908QH9Wg/VpqzI35R5dDqeuHYB24GdmLjDfZgYxHagE3jnKdHa3FxmNCY/3ARgam6UmZ77d3gQnuNOBbeWMnpbhFSdo9NZmNTBC8QaVqwDVuh06omK+0jKuxl4dDq1udZTFwHLcqODcGL2AjeElTqvEkUkI1JluHt12pQU/QL26XWDTgfwXQX/6qdTHRXtZci7qhhBjdJmg/IWijtzExQBrcwJ6EBVuOvShStOUCM0fApTe2qaY4+/F7hDmeLHbVU175WuW5nk4tA+AnwGc9Q+yPPZJzErcT8b7P0gEVKAUbH4TExs2jJgSkAeax8mKuPukeHQpoNPPVLVVeJFSFVE7rjBQuAa4EOYfBXVxAHgQWCVp0hlN6R6AvOxk+5ZnUSaWkJ9Jh/gpcBiTGKYSIX9mVlgE7AGeCikWNu3IdUbSK9BumRgFilGa5gPXADMA5qAkQP8jjuAjZjsuWsVPD5YMX8iJKEk1DS1eD1aNwKzMOnLZmBOn56ccwlrCljA8DHH3PdiNpLfSG22FXg2rNT2ajnWIUISimZIU4vXp3WDNjF0ozB5Aety4gr3c8uOYhLydwDtCtpCSrW5KhZBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBEARBECqH/wdp1gDAuoWC0gAAAABJRU5ErkJggg==
Next, you can run a simple helm update because we're not making any changes that require a restart, so there's no need for running ouctl again:
helm upgrade orchestra-login-portal tremolo/orchestra-login-portal -n openunison -f /path/to/values.yaml
Once the helm upgrade is complete, you can log into OpenUnison:
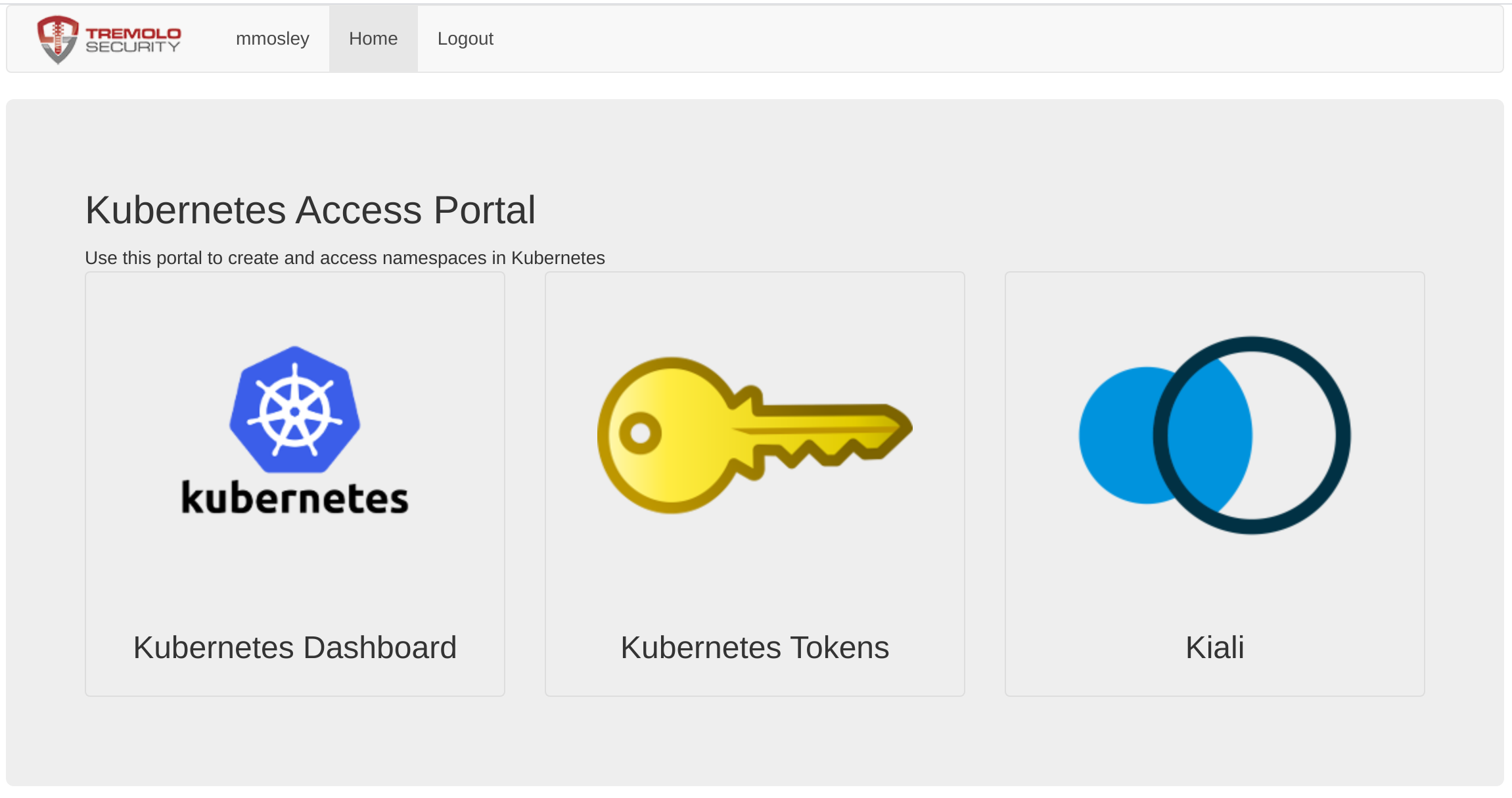
Clicking on the badge will open Kiali in a new tab. You'll see your username (which is sent to the API server) is in the upper right hand corner:
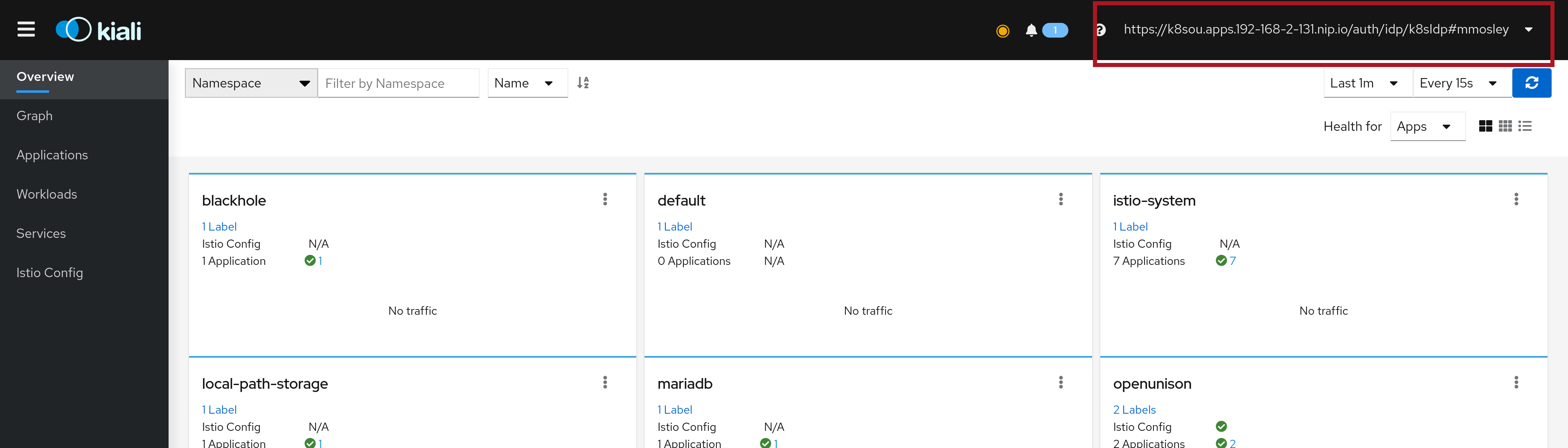
After logging out of OpenUnison, you will automatically be logged out of Kiali.